A Natural Language Processing Based, Variation Centric Input Handling Model for Social Computing Systems
Authors :
Nor Azura Husin and Balasubramaniyan Divager
Address :
Department of Computer science, Universiti Putra Malaysia, 43400 Serdang Selangor, Malaysia
Faculty of computer science and information technology, University putra Malaysia
Abstract :
Systems for social computing use environmental data to provide interactive applications that integrate software and computer power. Social computing systems with multi-input management have enhanced processing power and application speed because of their audible and readable characteristics. The multi-variant language processing problem in social computing that leads to computational failures is discussed in this article. A Variation-Centric Processing Model (VCPM) is used to mitigate breakdown errors caused by overlapping speech inputs in the aforementioned situation. By enhancing the similarity feature, the suggested model seeks to maximize the text input processing rate while accounting for different pronunciations and tones. The first input is regarded as the baseline upon which subsequent categorization and correlation are based. Based on the high processing rate, this initial reference is updated on a regular basis, after which additional classifications are carried out. Regressive mistakes, which are recognized as discrepancies in the processing of text and speech inputs, are used to reduce the variances in a regressive categorization pattern. By modifying the choices for regularized efficiency, this improves the efficiency of the social computing system. Processing rate, latency, error, accuracy, and dispersion are the measures used to validate the performance of this model.
Keywords :
NLP, Regression Learning, Social Computing System, Speech Processing.
1.Introduction
An interconnection among social application and computation systems is known as a social computing system. Social computing creates a connection between software and technology which provides better communication and services to users which helps to improve the whole experience [1]. A social computing system is a collection of many smart applications which are available on the web. It also provides better security and privacy policies to users which help to improve the overall performance of the application [2]. The social computing system is used in merging applications and provides a collaborative process among the social application which is used to improve user experience. Many social applications are done based on a social computing system such as Facebook and YouTube [3]. Managing a larger amount of data in an application leads to many problems during the computation process. Scale-independent storage (SCADS) is used in a social computing system to enhance the storage capacity which helps to increase the efficiency and effectiveness of the system. SCADS used SQL language to queue the data which are stored in the database. It also reduces the duplicate rate in the storage process which helps to increase the storage space for further uses [4, 5].
Natural Language Processing (NLP) is a process that is used to understand and manipulate data that are connected to a computer to generate a proper dataset for the data processing system. NLP is used to understand and analyze linguistic content which is sent by the users in an application [6]. NLP understands text or speech which is given by the users. NLP is mainly used to analyze human understanding capabilities to perform particular tasks. NLP is mostly used in web-based applications to understand users’ thoughts to provide better service at a needed time without any delay or failure [7]. NLP is widely used to understand, learning and produce human language processes. NLP-based application mostly uses a deep learning approach to avoid unnecessary problems and failures. NLP is used in social computing-based applications to understand the communication process among the users and is used to improve the overall performance in the communication process [8]. NLP also provides a communication process among the users and the machines or devices to understand the exact needs of users. In a social computing system, NLP is mainly used for the word segmentation process and keyword extraction process which plays a vital role in social applications. The learning algorithm is used in a social computing system for the word extraction process which helps to identify every detail of content or text before providing service to the users [9, 10].
NLP is used in social computing system-based applications to enhance the accuracy rate in providing services to the users by understanding the exact requests. Deep learning techniques are widely used in NLP applications which are used to improve the overall performance and efficiency of the system [11]. Deep learning-based NLP application analysis various features by performing some outlining process. Artificial intelligence (AI) is also used in NLP to understand the content of the text-based on knowledge [12]. AI utilizes human knowledge which helps to understand or calculate the text from a human point of view and provides an accurate set of data for the computation process. Cross-language information retrieval (CLIR) is used in social computing applications which are used to translate a foreign language into an appropriate form to understand for providing services to the users [13, 14]. Natural language is used here to understand the queries which are given by the users. CLIR is a knowledge-based approach that is used to understand the lexicon-grammar to formalize unknown content. CLIR improves the overall accuracy rate in the translation process and also increases the efficiency of the applications [15].
2. Related Works
Li et al. [16] proposed a deep neural network-embedded Internet of Social Computing Things (NeSoc) for sustainability prediction process. Deep Neural Network approach is used here to calculate the computation process which is available in the model. It is used to calculate and collect data which are used for computation process. Experimental results show that the proposed NeSoc method increase the overall performance of the system and also reduces computation cost.
Ait-Mlouk et al. [17] introduced a knowledge graph by based on chatbot approach (KBot) for natural language understanding (NLU) process. Intent classification method is used in NLU for providing better understanding over the users. The proposed KBot method increases the overall flexibility, reliability and efficiency of NLU process. When compared with other knowledge-based techniques, the proposed KBot method increases the performance of the system by providing proper interactive process.
Baydogan et al. [18] proposed a novel approach named Ant lion optimization (ALO) and moth flame optimization (MFO) algorithm for automatic Hate speech detection (HSD) process. The proposed approach is used to identify HSD issues such as swearing, intolerance, insults, and humiliation. ALO method is used to increase the accuracy rate in detection hate speech. It is an efficient and flexible approach while provides a better detection process for automatic HSD. Experimental results show that the proposed method increase the overall performance of the system.
Jindal et al. [19] introduced a novel semiautomatic for ontology or terrorism domain analysis process which is used in social media analytics. Terrorism attacks in social media are one of the dangerous attacks, the proposed method is used to prevent users from the attackers and secure user’s personal details. Query-based system is used here to extract the knowledge or details which are available in the database. Fluent editor is used in the proposed method to identify the terrorism attack by understanding the content which are sending by the users.
Paredes et al. [20] proposed a new malicious behavior detection process for social medial application by using hybrid knowledge driven system. The proposed method is used to identify the uses that posted or published fake news in social media networks. Also detect the fake news reporter and prevents the users from viewing the fake news. Experimental results show that the proposed method increases the accuracy rate in detection process and improves the efficiency of the system.
Chen et al. [21] introduced a new method named FritzBot by bidirectional long short-term memory (BiLSTM) network. Conditional random field (CRF) is also in FritzBot to train the dataset which are available in the database for detecting fake texts. FritzBot generates a circuit by analysing the actual text which is sent by the users in social media. Experimental results show that the FritzBot method increases the overall performance of the system by reducing the computation cost, latency rate and energy consumption rate in detection process.
O’Halloran et al. [22] proposed a multimodal approach which is used for analyzing process in social media application. The proposed method is used to understand the communication process among the users and the organization which helps to produce a proper mapping system. The proposed method improves the overall computation process in big data analytics process.
Tsuji et al. [23] introduced a blueprint for computational model which is for social learners in social interaction process. The proposed method is used to identify the communication process among the users which widely used by social learns to identify the fake news reporters. Computational mechanism is used here to understand the exact content of the text and helps to extract the information which is available in the database. Experimental results show that the proposed method increases the overall performance of the system.
Alkouz et al. [24] proposed a road traffic analysis process named SNSJam by using cross-lingual data for social media networks. Cross-lingual data are collected from dynamic source which plays a vital role in classification process. Location recognizer is used in SNSJam to locate the traffic jams which are occurred in roads. The proposed method also identifies the cause of traffic jams and produces a solution to avoid unwanted traffic jams. When compared with other methods, the proposed SNSJam method increases the accuracy rate in traffic jam detection process.
Alarifi et al. [25] introduced an optimized cognitive-assisted machine translation (MT) approach for natural language processing. Machine learning approach is used in the proposed to understand the high-quality content and helps to translate the actual details of the text. A smart decision-making tool is used in the proposed MT approach to understand the efficiency and effectiveness of the content. Experimental results show that the proposed method increases the overall performance of the MT approach by reducing the computation cost and by increasing the accuracy rate in translation process.
Al-Makhadmeh et al. [26] proposed a new automatic hate speech detection method by using natural language processing. The proposed method is used in social media applications to predict the hate speech by analysing the good speech frames. An effective learning process is used here to classify the speech by based on good, bad, hate or informal language. Experimental results show that the proposed method increases the overall accuracy rate in detecting hate speech which helps to improve the performance of the social media application.
Ni et al. [27] proposed a natural language understanding (NLU) approach which is used for Internet of Things (IoT) voice interaction process by using joint task of intent detection method. Slot filling joint task is also used in NLU for human interaction process in IoT based applications. Intent detection process is used to improve the slot filling task which is used to provide significant building for human voice interaction process in IoT. When compared with other approaches, the proposed NLU increases the joint model’s accuracy rate and provide better interaction process of users.
Fontes et al. [28] introduced a deep learning framework for utilizing Twitter data to examine urban mobility. It uses Natural Language Processing (NLP) methods for data cleansing, tweet classification, and emotion analysis. Using this approach, we may better understand public opinion and trends in urban mobility by comparing the accessibility of three major cities: London, Melbourne, and New York. Transportation planners can benefit from its high accuracy in text classification and ability to aggregate data in near real-time. However, there needs to be more research on scalability and generalizability.
Li et al. [29] proposed an interaction graph network (IGN) for adverse drug reaction (ADR) recognition process. ADR detection is widely used in social media to address the users by with the help of surveillance cameras. The proposed IGN is used to identify the lexicon type of drug which is one of the difficult tasks to perform. Lexicon is identified by encoding the context which is available in the database by using graph attention network. Experimental results show that the proposed IGN method increases the accuracy rate in detecting ADR.
3. Proposed Model
The proposed VCPM model is designed to improve the classification and correlation accuracy of the voice inputs for backhauling interactive applications. The NLP application model regulates through assimilating software and computational abilities in an available and readable feature on better accuracy for its functions. The proposed model of VCPM language detecting method is designed to control the functions of the computing systems employed in a social computing systems. In a social computing system environment, voice capturing devices such as Speakers, Cortana-Microsc, Apple Home pod, Amazon Echo, Google Home, etc. are used that is recorded or recognized through computing systems. The computing systems are a combination of software and hardware terminals to recognize and gather voice input accumulated from the computing system environment. The voice recognition is equipped with signals detecting units to record or recognize information such as voice, text, etc. In the proposed VCPM precise output and computing systems are devised using the processing recommendations based on the interactive applications. A social computing system framework consists of centralized computing system unit that manages the operations of the devices through voice input and text (V). The function of the computing systems is regulated using wireless signals and Google keyboard. The VCPM method functions between interactive applications and social computing systems. VCPM is one such method that ensures use of regression learning for attribute classification and correlation of voice input. The proposed model is illustrated as in Figure 1.
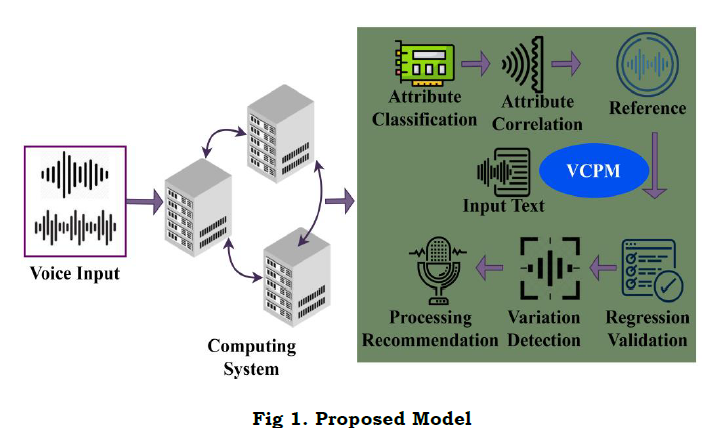
. The proposed model intakes voice commands or voice notes for performing defined operations. The computing system classifies the available attributes for correlation and reference finding. Based on the identified references, the regression learning and variation detection are performed. The recommendations are provided based on the achievable accuracy ensured in the process (Figure 1). The processing function of VCPM in NLP based application acquires inputs through voice signals (VI) observed in the human. The voice inputs are performed for attributes classification and correlation using regressive learning using the features audible and readable. The attributes classification output is aided for detecting the observation through attributes correlation from the gathered information. The function of VCPM is notices the multi-variant language processing problem in social computing that outputs in computational breakdowns where the voice initially filtered. The input of voice signal is represented as
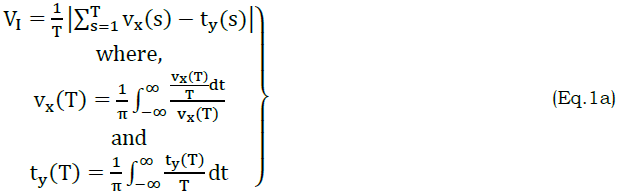
Where, the variables vx(s) and ty(s) represent the voice and text of the VI with respect to wavelength transform in x and y planes and s is the observed signal, respectively. If x and y planes are increasing and decreasing edges with respect to time and then x∈[0,∞] and y∈[−∞,0] and therefore,

Based on the above equation (2), the initial voice input is suppressed for all vx(T)+ty(T) that represents a overall instance relies on x and y wavelengths for a given interval of time on (q×T). Here, q is the total queuing process. The queuing process is computed to reduce the processing rate present in VI. Voice input is due to the decent quality sound captured in the computing system while acquiring VI in any time interval T. This computing system follows a high processing rate of queuing that is computed as follows.
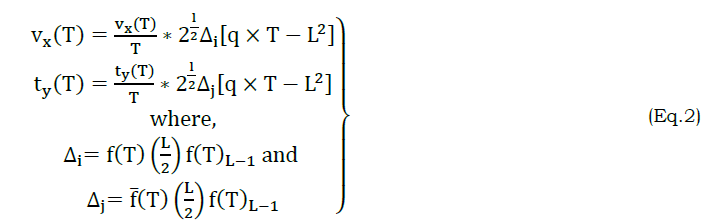
Based on equation (2), the variables Δi and Δj is the queuing transform function for low and high processing rate. The factors of f(T) and f̅(T) represents the frequency of transformation and routine transformation functions of Δi and Δj. From the sequence of occurrence of the partial wavelength (i.e.) x or y, the frequency of input transformation and routine transformation functions are used. Where, the variable L denotes the voice input length used in both the processing of wavelength identification. Here, the frequency based VI is defined as
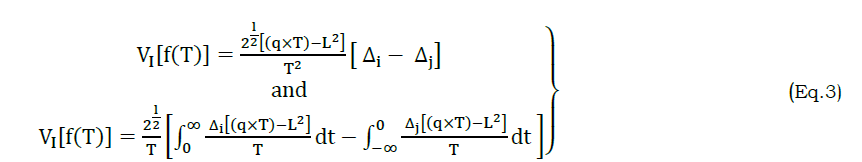
From the computational breakdown of voice input less VI[f(T)] that is accessed after applying queue. From this multi-input management of VI[f(T)], two features namely audible and readable are extracted for further attribute classification. The audible (AD) and readable (RD) features is computed as
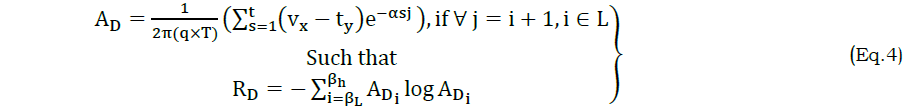
Where, e is the error occurrence at the multi-input management processing, α is the point lies on the normal plane, βh and βL are the high and low frequency rate of AD observed. The log recognition of AD and RD for the f(T) is estimated as

This log voice recognition is computed for synchronization RD[f(T)] and RD alone with the various time intervals and time instances. The attribute classification process is based on AD and RD[f(T)] using regression learning. The attribute classification process based on log recognition is presented in Figure 2.
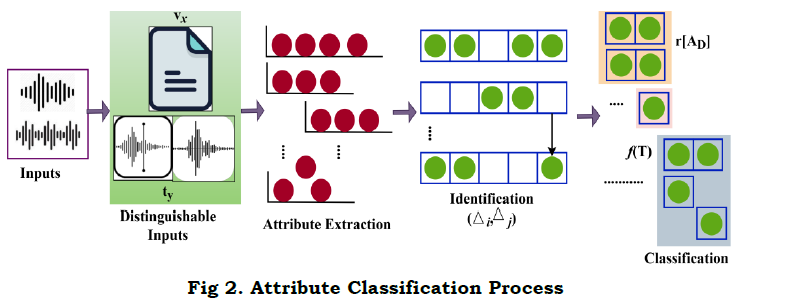
The inputs are first distinguished for vx and ty for extracting available attributes. The queuing process is responsible for defining the functions in distinguished intervals, for further classification. This attributes classification helps to maximize the text input by augmenting the similarity functions regardless of varying tones and pronunciations for all vx(T) or ty(T) or both wavelength (Figure 2). In this attribute classification, the similarity features are independently analyzed at each level followed by the joint attribute classification. The initial level is considered as the instance based on which the further processing take place. The first instance of reference are determined as in following equation (6a) and (6b) for AD and RD[f(T)].
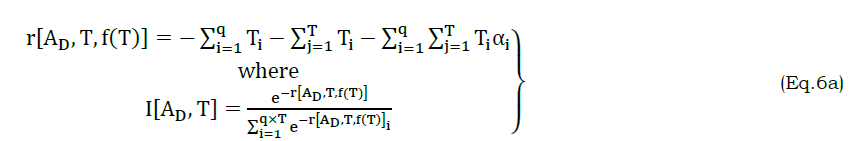
As per the above equation (6a), r represent the regression function for AD and I is the first input of reference at T. Similarly, the first instance of inputs and consequence are given for RD[f(T)] as
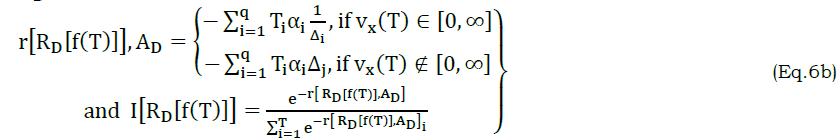
From equation (6b) the similarity verification and reference of the regression learning is presented such that r[ RD[f(T)],AD] is evaluated for both the wavelengths∈ VI[f(T)]. This process helps to determine the computing system based on T to ease possible attribute classification instances. The similarity verification of the regression learning process based on VI[f(T)∈[−∞,∞]] and vs∈[0,∞] or vs∉[0,∞]. The condition of vs∈[0,∞] succeeds a stage of [−∞,0] that inversely denotes ty at a given time instance T. The condition of the VI[f(T)] is autonomously using I[.] where in the sequence of I[.]∗ represents that the condition of vs∈[0,∞] is experienced and therefore the existing (previous) I[.] does not keep for further computations. As per the above derivation, vs∈[0,∞] are identified as the regressive errors ty∉[0,∞] is another choice and therefore, now vs∈[0,∞] and vs∉[0,∞] is considered. These regressive errors (RE) are mismatched with the voice and text input process to obtain the final solution (z). Hence, the attribute classification and correlation output sequence of {c1to cq×T} for both the voice input and text is estimated. The attribute classification and attribute correlation sequence output along with highest accuracy α that are estimated as
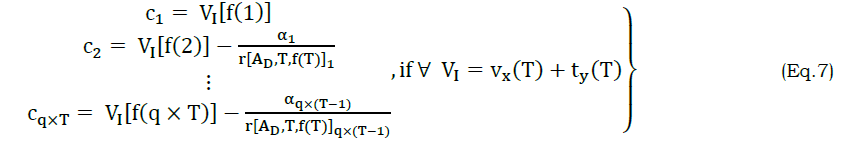
Instead,
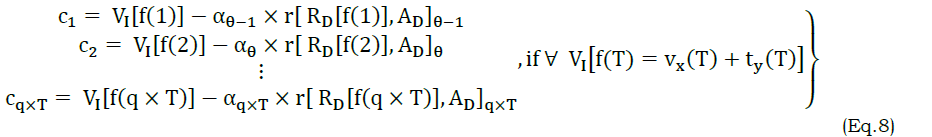
In the above equations (7) and (8), θ is the point at which VI[f(T)] is determined from VI=vx(T)+ty(T) to vx(T) or ty(T) alone. If it comes to the reference of regressive validation, then similarity is the considerable factor. The correlation process using regressive learning is presented in Figure 3.
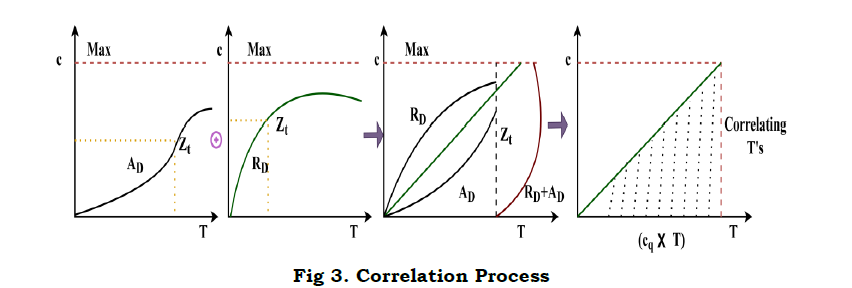
In the correlation process, the maximization is focused for the reference inputs in different T. The correlation in cq×T is achieved for non-overlapping RD and AD such that the joint interference are augmented for VI. Therefore, VI[f(T)] is considered as the performance of T in improving processing rate (Figure 3). This is ensured for a time interval and then the first reference is changed periodically based on the high processing rate and then further classifications are performed. Here, the first reference output for VI[f(T)]≠vx(T) is given as
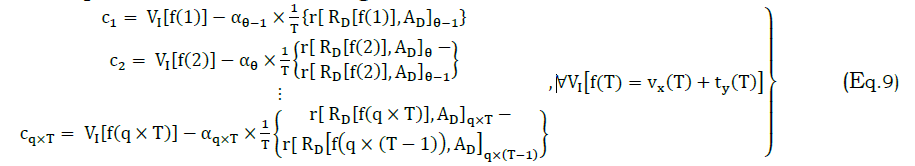
Where, the variable α is estimated as in the following equation (9)
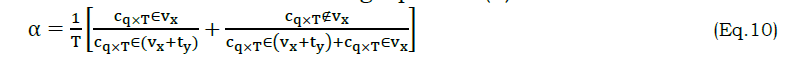
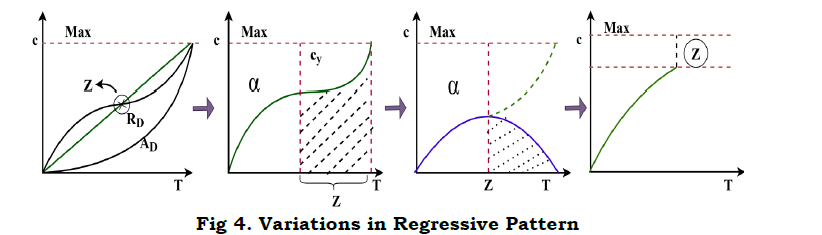
The condition on the x,y plane represents the periodical changes of θ such that if cq×T∉vx or cq×T∈vx≤θ The autonomous computing system with respect to t differentiation is increased as the single swiftness of the result z. This solution is not the last as the last obtaining is based on ztdt using the attribute classification and correlation with high accuracy estimation. Similarly, periodical change in reference differ the precision of RE and PR by evaluating α with the C VIbased on the solution of ztdt computing system analysis. The variation due to overlapping using regressive learning is presented in Figure 4.
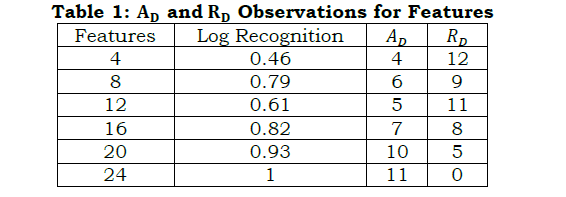
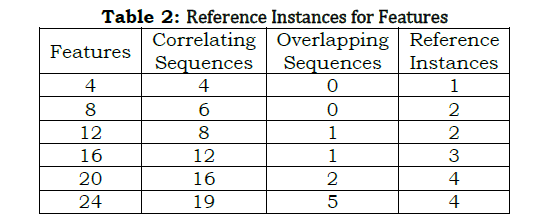
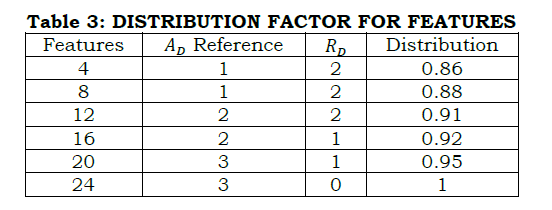
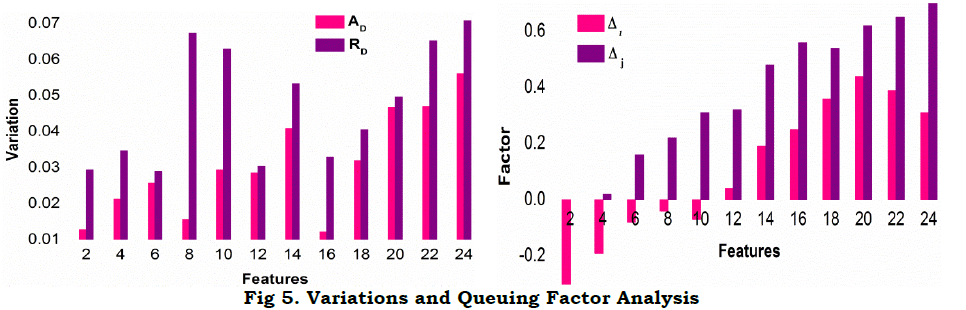
The correlation detection method is presented for Z and T wherein the α maximization is required. In the different combinational inputs, the precise Z is alone identified for reducing cy and its variations. The method of C VI+(1−α)Cx overlaps at any t such that, either C VIor Cx is increased (Figure 4). In this model, the reference with high PR is augmented for the social computing system. The following equation represents the regressive validation for deriving z based on the system efficiency, respectively. In this sequence of output of the computing system function as α=r[.]=1, the solution does not adapting any readable or RE. In the similar manner, the computing system assessment of Cx, Cy and z as per α is denoted, respectively. In this time the variation detection of the classification pattern is as follows In above equation (13), the condition (1−α)T serves as the processing recommendations. This condition is identified as mismatched in processing voice and text inputs using RE that aids the social computing system efficiency by changing the decisions for regularized efficiency of αT for processing recommendations Cy outputs computed as From the classification pattern functions solution of z for all cq×T∉vx or cq×T∈vx≤θ Table 1 presents the RD and AD classifications for differed features observed. The RD[f(T)] is indefinite as RD and AD is uncertain wherein the further processing is initiated. This distinguishes Z based on classification alone and thus, if AD varieties, then RD shows up the difference. This is observed until vx≤θ is satisfied. On the other contrary, if θ An observation analysis for the reference instances are presented in Table 2 for different features. The overlapping in Ztdt is identified based on the C1 to cq×T instances. This is observed in different sequence is augmented without compromising Z in cy outcomes, maximizing the references. The distribution factor observed for different features is presented in Table 3. The input distribution observed in different features extraction is presented in Table 3. The distribution relies on AD and RD based on (q×T) observed. In the αT maximizing instances, the RD[f(T)] is considered for defining further Δi or Δj. Therefore based on the queuing factor, the reference is defined for r[.] until c=1is achieved. This requires concurrency in Z detection wherein the input is overloaded for the observedZtdt. Therefore, the distribution is high if both AD and RD is balanced with the previous and current f(T). Figure 5 illustrates the analysis for variations and queuing factor under different features. Figure 5 presents the (AD,RD) variation, and (Δi,Δj) factor for different VI features observed. The AD feature is classified based on r[AD,T,f(T)] for which Z in equation (9) and (13) are considered. AnZtdt is required of a RD overlaps AD in which a non-linear results is obtained. The Δi or Δj is utilized for any one of Ad or RD for which the f(T) is positive. Contrarily for both the inputs, the AD,RD based on the reference, the distribution is performed. In distinct classification sequences, the (Δi,Δj) factor is balanced to be attained in a positive hike maximizing the accuracy.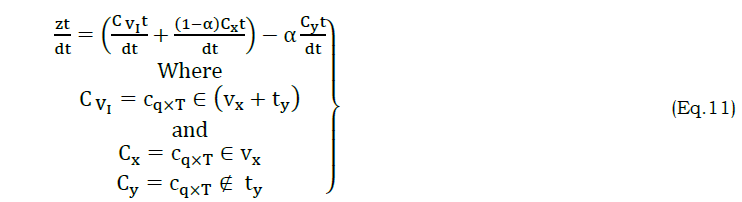
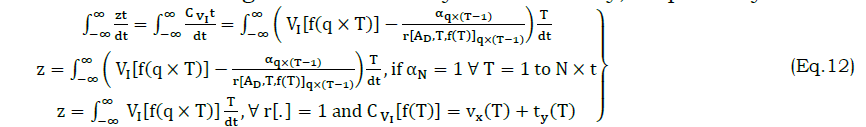
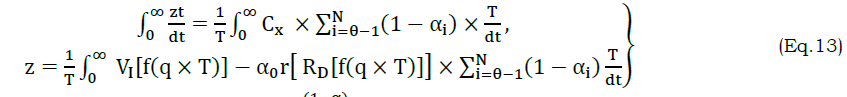
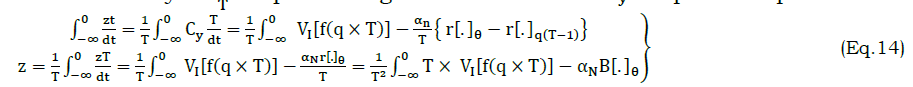
4. Results and Discussion
This subsection describes the VCPM’s performance using MATLAB simulations. For this simulation, voice command and text inputs from [30] are utilized for operating mobile devices and Alexia. The processing is performed for 260 combined inputs, from which 24 features are extracted. The voice notes vary from 1s to 14s for providing commands in operating devices. With this implication, the metrics processing rate, delay, error, accuracy, and distribution are analyzed. For a better decision, above metrics for the existing ALO+MFO [18], KNLPEDNN [26], and OSMT-SMT [25] are compared.
a. Processing Rate
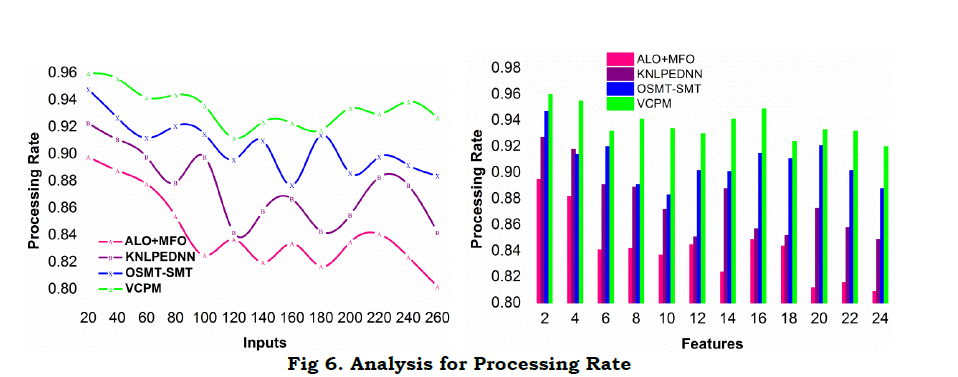
Figure 6 illustrates the comparative analysis for processing rate under different inputs and features. In the proposed model, 𝑣𝑥(𝑇) and 𝑡𝑦(𝑇) are distinguished for their 𝐴𝐷 and 𝑅𝐷 respectively, the 𝑐𝑞×𝑇 process is independently performed for the above features. In the first process, 𝑟[𝐴𝐷,𝑇] and 𝑟[𝑅𝐷[𝑓(𝑇)]] is estimated without 𝛼 consideration. Contrarily, in the 𝑞×𝑇 validation, the 𝑍𝑡𝑑𝑡 defines the existence of 𝑍 under regressive incidents, preventing its influence on 𝛼. Therefore, in the variation detection process the processing is improved from the 𝑅𝐷[𝑓(𝑇)] for 𝑅𝐷 in a non-regressive manner. In the consecutive sequences, the 𝑍𝑡𝑑𝑡 is identified under controlled variations, preventing failures. Therefore, (Δ𝑖,Δ𝑗) instances for single input based on features are improved. This improves the feature based correlations as in equations (7), (8) and (9). The empty slot for correlating sequence validation requires further processing under distinguished 𝐴𝐷,𝑅𝐷 maximizing the processing rate.
b. Delay
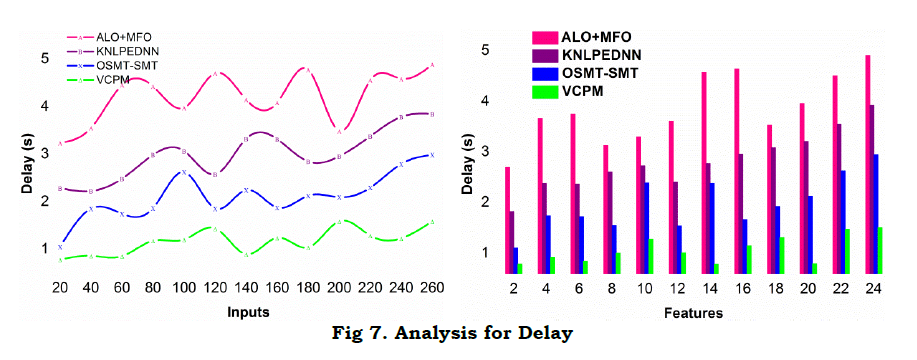
A comparative analysis for delay is presented in Figure 7 observed for different features and inputs. As seen in the illustration, the proposed model achieves less delay compared to the other methods. In the proposed model, the c′s sequence is distinguished for VI=vx(T)+ty(T),θ and 1T respectively. This classification is required for VI[f(T)≠vx(T) and hence the variations are suppressed such that Δi and Δj are varied based on multiple AD and RD. The regressive sequence verifies α based on all these instances such that RD[f(T)] is required in mitigatingZtdt. Therefore, the (Vx+ty) induced in error factor is confined under either of the equation (7), (8), or (9). Therefore, one sequence is suspended without maximizing the variation. Hence forth, delay is observed in any one instance, preventing additional computations. Depending on αT in all the three variations, the f(T) is remodeled for adapting delay less processing. Hence the α retained intervals are modeled based on distinct cy for preventing additional delay. This is harmonized for the features and inputs observed in different instances.
c. Error
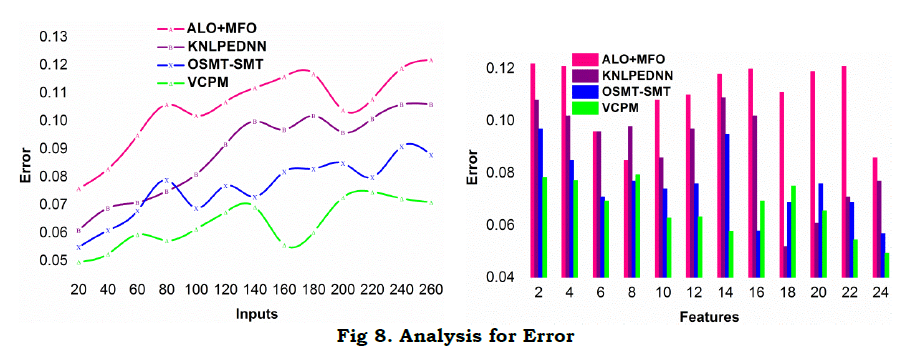
The proposed model achieves less error by maximizing α by mitigating Z under different conditions. First the Ztdt is analyzed for variations in regression and classification patterns. In the continuous iterations, ∀T∈1 to T×q, the overlapping case is identified for R∈ instances. Based on the iterations, cx∈vx and cx∉ty are identified without cvx estimation. This estimation does not detect any possible correlation in c1 to cq×T instances. Contrarily, the overlapping (1−α) in cx is detected for identifying Z in different classifications. This is mitigated underαT variations. The consecutive iterations correlates with RD[f(T)] or Δi and Δj for preventing final errors. The regression function distinguishesZtdt and Z for cy for reducing (1−αT) and hence improving c(q×T). The correlation for distinct features increases the error decreases and hence the successive possibilities are validated. The consecutive sequences are validated based on RD[f(T)] such that Δi and Δj are reorganized in RE. This implication is pursued only if the inputs increase for which Z [as in equation (13)] is observed. Therefore, the classification is performed based on features, for reducing errors (Figure 8).
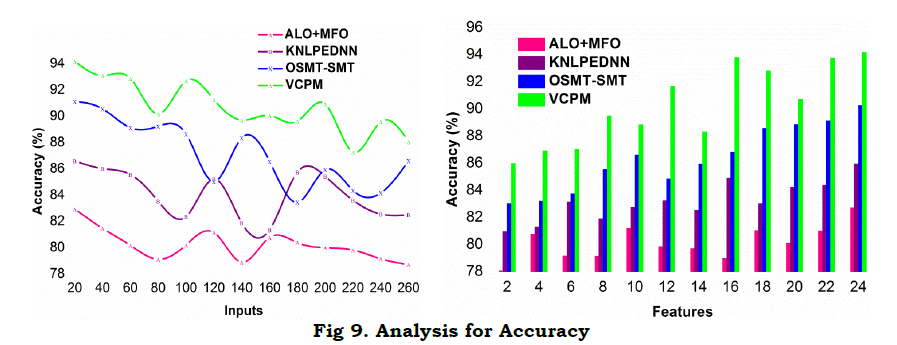
d. Accuracy
The proposed model achieves high accuracy for different features and inputs as presented in Figure 9. The α focused performance of the regression is presented using Z andZtdt validations in this model. Depending on the available (1−α)T estimations, the further RD and AD differentiation is performed. In the sequential process, cq×T is ensured for satisfying α=r[.]=1 wherein the accuracy is maximized. Regardless of the f(T) for the modified sequences, RD[f(T)] is confined based on the independent references estimated in equations (6a) and (6b). Therefore, as defined for the regressive sequences, c1 to cq×T is classified for either of Z as estimated in equations (12), (13) or (14). In this process, CvI∈cq×T αN=1,and vx≤θcq×T are independently defined for leveraging the α factor. However as the inputs increase, the α factor is initially unstable due to classification issues wherein it defaces. This is mitigated based on different intervals such that error due to Ztdt is confined. The process is repeated until the c for its maximum limit is achieved as distinguished by the correlating Tfactor. Hence the pursuing regression is modified based on Z and previous r[.]=1 as defined by f(T). This maximizes the accuracy factor for the proposed model.
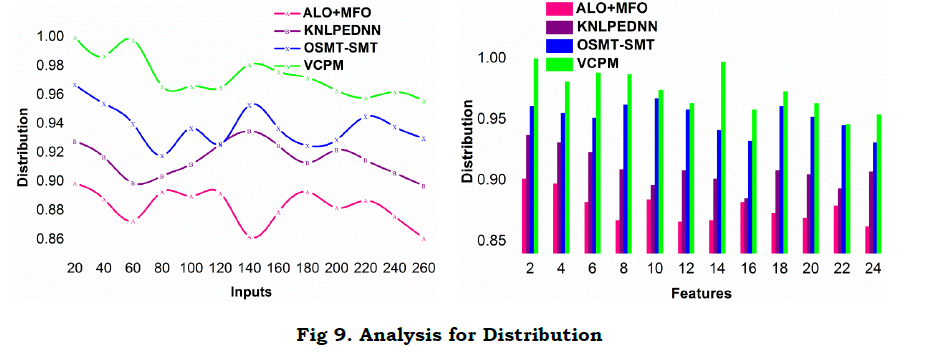
e. Distribution
The proposed model is found to have high input distribution factor compared to the other methods. In the computational instances, the Δi and Δj determines the input requirement and RD[f(T)] validation. The input is initially not classified wherein RD⨁AD jointly performs the classification without leveraging the error. In the successive classifications as in equation (12), (13) and (14), the process is independent accepting multiple inputs. Therefore, the need for inputs and feature extraction is high compared to the previous f(T). This jointly exploits vI=vx(T)+ty(T) in f(T) defined instances and hence (q×T) is shared for the above AD and RD defined regressions. In the proposed model, the incoming VI are allocated with the existing RD or AD processing instances, classified by the features. This provides space for further inputs in the class increasing the distribution. Another classification is the concurrent utilization of the r[.] as defined in equations (6a) and (6b). Therefore, the available and Δi and Δj induced VI are distributed swiftly awaiting further q×T. Therefore, this factor leverages without variations in distingued inputs and features. Tables 4 and 5 present the comparative analysis summary for different inputs and features respectively.
5. Conclusion
For addressing the error-based issues and variations in multi-input voice processing, this article introduced a variation-centric processing model. In this model, the voice and text inputs are classified for their available features. The identified features are used for defining independent reference plots for detecting variations. In the plot mapping, the linear regression learning is induced for identifying correlation and overlapping sequences. Based on the regression output, the reference points are modified for which the variations are processed using different conditions. In this process, accuracy and processing rate are operated for modifying the reference and hence the variations in joint input processing are mitigated. The regressive classifications result in error, variation, and overlapping reference estimation for which the computations are repeated until maximum processing and accuracy are achieved. From the experimental results, it is seen that for the varying features, the proposed model achieves 7.13% high processing rate, 10.26% less delay, 6.79% less error, 7.88% high accuracy, and 5.4% high distribution.
References :
[1]. Seneviratne, O., Adams, K., & McGuinness, D. L. (2023). Accountable Bench-to-Bedside Data-Sharing Mechanism for Researchers. ACM Transactions on Social Computing.
[2]. Dragos, V., Battistelli, D., & Kellodjoue, E. (2020). A formal representation of appraisal categories for social data analysis. Procedia Computer Science, 176, 928-937.
[3]. Zhang, Q., Tang, C., Bai, T., Meng, Z., Zhan, Y., Niu, J., & Deen, M. J. (2021). A two-layer optimal scheduling framework for energy savings in a data center for Cyber–Physical–Social Systems. Journal of Systems Architecture, 116, 102050.
[4]. Valinejad, J., Mili, L., Yu, X., van der Wal, C. N., & Xu, Y. (2023). Computational social science in smart power systems: Reliability, resilience, and restoration. Energy Conversion and Economics.
[5].Nikravan, M., & Kashani, M. H. (2022). A review on trust management in fog/edge computing: Techniques, trends, and challenges. Journal of Network and Computer Applications, 204, 103402.
[6]. Shahbazi, Z., & Byun, Y. C. (2021). Fake Media Detection Based on Natural Language Processing and Blockchain Approaches. IEEE Access, 9, 128442-128453.
[7]. Yuvaraj, D., Ahamed, A. M. U., & Sivaram, M. (2021). A study on the role of natural language processing in the healthcare sector. Materials Today: Proceedings.
[8]. Nicolas, C., Kim, J., & Chi, S. (2021). Natural language processing-based characterization of top-down communication in smart cities for enhancing citizen alignment. Sustainable Cities and Society, 66, 102674.
[9]. Mazzei, D., Chiarello, F., & Fantoni, G. (2021). Analyzing social robotics research with natural language processing techniques. Cognitive Computation, 13(2), 308-321.
[10]. Franzosi, R., Dong, W., & Dong, Y. (2021). Qualitative and quantitative research in the humanities and social sciences: how natural language processing (NLP) can help. Quality & Quantity, 1-31.
[11]. Song, W., Guo, J., Fu, R., Liu, T., & Liu, L. (2020). A Knowledge Graph Embedding Approach for Metaphor Processing. IEEE/ACM Transactions on Audio, Speech, and Language Processing, 29, 406-420.
[12]. Dessì, D., Osborne, F., Recupero, D. R., Buscaldi, D., & Motta, E. (2021). Generating knowledge graphs by employing Natural Language Processing and Machine Learning techniques within the scholarly domain. Future Generation Computer Systems, 116, 253-264.
[13]. Jackson, P. C. (2021). On achieving human-level knowledge representation by developing a natural language of thought. Procedia Computer Science, 190, 388-407.
[14]. Li, H. X., Lu, B., Chen, X., Li, X. Y., Castellanos, F. X., & Yan, C. G. (2021). Exploring self-generated thoughts in a resting state with natural language processing. Behavior research methods, 1-19.
[15]. Alhogail, A., & Alsabih, A. (2021). Applying machine learning and natural language processing to detect phishing email. Computers & Security, 110, 102414.
[16]. Li, Q., Song, Y., Du, B., Shen, Y., & Tian, Y. (2020). Deep Neural Network-Embedded Internet of Social Computing Things for Sustainability Prediction. IEEE Access, 8, 60737-60746.
[17]. Ait-Mlouk, A., & Jiang, L. (2020). KBot: a Knowledge graph based chatBot for natural language understanding over linked data. IEEE Access, 8, 149220-149230.
[18]. Baydogan, C., & Alatas, B. (2021). Metaheuristic Ant Lion and Moth Flame Optimization-Based Novel Approach for Automatic Detection of Hate Speech in Online Social Networks. IEEE Access, 9, 110047-110062.
[19]. Jindal, R., Seeja, K. R., & Jain, S. (2020). Construction of domain ontology utilizing formal concept analysis and social media analytics. International Journal of Cognitive Computing in Engineering, 1, 62-69.
[20]. Paredes, J. N., Simari, G. I., Martinez, M. V., & Falappa, M. A. (2021). Detecting malicious behavior in social platforms via hybrid knowledge-and data-driven systems. Future Generation Computer Systems, 125, 232-246.
[21]. Chen, T., Xu, L., & Zhu, K. (2021). FritzBot: A data-driven conversational agent for physical-computing system design. International Journal of Human-Computer Studies, 155, 102699.
[22]. O'Halloran, K. L., Pal, G., & Jin, M. (2021). Multimodal approach to analysing big social and news media data. Discourse, Context & Media, 40, 100467.
[23]. Tsuji, S., Cristia, A., & Dupoux, E. (2021). SCALa: A blueprint for computational models of language acquisition in social context. Cognition, 104779.
[24]. Alkouz, B., & Al Aghbari, Z. (2020). SNSJam: Road traffic analysis and prediction by fusing data from multiple social networks. Information Processing & Management, 57(1), 102139.
[25]. Alarifi, A., & Alwadain, A. (2020). An optimized cognitive-assisted machine translation approach for natural language processing. Computing, 102(3), 605-622.
[26]. Al-Makhadmeh, Z., & Tolba, A. (2020). Automatic hate speech detection using killer natural language processing optimizing ensemble deep learning approach. Computing, 102(2), 501-522.
[27]. Ni, P., Li, Y., Li, G., & Chang, V. (2020). Natural language understanding approaches based on joint task of intent detection and slot filling for IoT voice interaction. Neural Computing & Applications, 32(20).
[28]. Fontes, T., Murçós, F., Carneiro, E., Ribeiro, J., & Rossetti, R. J. (2023). Leveraging Social Media as a Source of Mobility Intelligence: An NLP-Based Approach. IEEE Open Journal of Intelligent Transportation Systems.
[29]. Li, Z., Yang, Z., Wang, L., Zhang, Y., Lin, H., & Wang, J. (2020). Lexicon Knowledge Boosted Interaction Graph Network for Adverse Drug Reaction Recognition from Social Media. IEEE Journal of Biomedical and Health Informatics.
[30]. Speech_commands. (n.d.). Retrieved October 20, 2023, from TensorFlow website: https://www.tensorflow.org/datasets/catalog/speech_commands